Whether for internal employees or external customers, businesses should seek out multi-factor authentication solutions that present a frictionless experience. This means that it must be able to support a wide range of applications without the need for lengthy IT projects, syncing disjointed data and expensive hardware.
It also must be capable of detecting login attempts that may be nefarious and take the necessary action, including requiring additional MFA factors. To learn more, download our free Requirement Checklist:
User Experience
Today’s teams work in a variety of ways – on the go or from home, on their company or personal devices, with various operating systems and browsers. This complex landscape designed to streamline and optimize work often introduces security vulnerabilities that require more than just a username and password to resolve.
SSO and MFA are an excellent combination to ensure secure access to apps and websites while reducing the number of passwords a user has to manage. But evaluating MFA and SSO solutions should go beyond security requirements and complexities to address the user experience as well.
Users want a convenient and hassle-free authentication process that allows them to securely access their apps and websites without any interruptions in their workflow. A solution that offers a flexible authentication flow and supports a range of MFA factors is essential for this user experience.
It’s also important that the MFA solution is cloud-agnostic and can integrate with any type of identity repository – whether it’s an on-premise Lightweight Directory Access Protocol (LDAP) server, SAML-based integration or an external identity provider. This way you’re not locked in to a particular platform and can easily expand your MFA capabilities as your business grows. The MFA solution should also be able to support a passwordless login and help reduce the number of calls to your helpdesk caused by forgotten or lost passwords.
Security
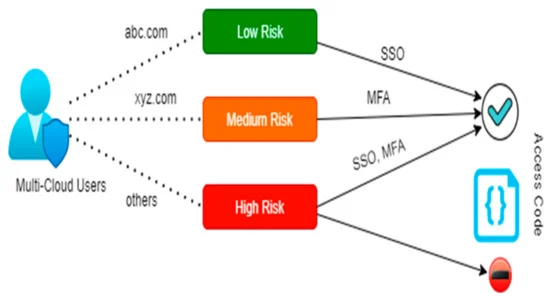
A robust MFA solution uses a dynamic, risk-based approach to significantly strengthen authentication security. It leverages contextual attributes like user and device behavior, location, phishing indicators, and brute force attack methods to determine on-the-fly whether access should be denied or stepped up.
MFA also adds an extra layer of protection by requiring users to use another factor of verification such as one-time codes sent to their mobile devices, or biometrics to prove identity. This significantly reduces the impact of breaches caused by stolen or weak passwords. For example, the 2020 Verizon Data Breach Investigations Report found that 81% of hacking-related breaches used compromised credentials.
The right MFA and SSO solution should allow you to set up granular access privileges by role, department or seniority level. This makes it easy to remove a user’s login rights when they leave your organization, or when they become a security threat. This centralizes access management while ensuring that users only have access to applications they need.
The right MFA and SSO solution will also offer a passwordless authentication option that eliminates the need to use an internal or external password manager. Be wary of SSO providers who claim to have this capability if they rely on shared secrets or a token system – which will still introduce vulnerability. A fully integrated MFA and SSO solution such as LoginRadius CIAM can provide a seamless, secure experience while eliminating shared secret vulnerabilities from the login process.
Convenience
MFA adds layers of verification to account and system access, making unauthorized access much harder even if passwords are compromised. But, if it requires employees to follow cumbersome protocols like constantly changing or adding new authentication factors, that can lead to employee frustration and fatigue. Choosing a solution that offers a seamless, easy-to-use MFA experience is critical for maximizing adoption and security benefits.
Single sign-on (SSO) centralizes authentication and makes logging in to connected applications easier for end users by allowing them to access everything from their email to the software systems they use to do their jobs. However, this can also be a security risk as it creates a single point of failure and increases vulnerability if that application is breached.
Choosing an SSO and MFA solution that is built on a robust Identity as a Service (IDaaS) platform can reduce the risks and complexity associated with SSO, while delivering the best user experience possible. For example, an IDaaS platform like LoginRadius includes a comprehensive set of MFA and SSO authentication methods that are simple to deploy across your entire organization with no additional planning or deployment.
In addition, an IDaaS platform can make it much easier for administrators to enforce policies and access controls uniformly for both internal workforce users and customer users without having to re-provision each one individually. This can significantly cut down on helpdesk activity and support costs by reducing the number of password resets and other security issues that need to be addressed.
Integrations
The right MFA solution needs to be able to integrate easily with your existing identity management system and support the authentication methods that are in use by your users. It should also let you expand with additional factors without requiring you to redeploy, procure, and integrate systems manually or to keep syncing disjointed data for years.
It is important to ensure that the MFA solutions you select can be used in conjunction with SSO, which allows a single login to access multiple applications. This helps to mitigate the risks of account takeover attacks and provides a seamless login experience for your users.
A good MFA and SSO solution will allow you to choose from a wide range of user-friendly authentication methods. That way, you can provide your employees with the security options that suit their specific needs and preferences. For example, some may prefer to authenticate with push authentication on their mobile device, while others may prefer a hardware token or even voice verification through a landline phone.
Choosing the right MFA and SSO solutions can be complex, but it is essential that your business takes the time to carefully consider both security requirements and usability. Then, you can be confident that your MFA and SSO strategies will not only prevent unauthorized access but also minimize the impact on employee productivity.